Website Penetration Testing: How to Protect Your Reputation
Protect your website and your reputation with pentesting Website penetration testing, better known as pentesting,...
Leverage our extensive HubSpot development experience to build anything in HubSpot CMS.
Redesign a website with a theme, build a custom one, or migrate to HubSpot CMS
Automate workflows with apps, custom objects, HubSpot API integrations & CRM extensions
Get our Level Up HubSpot theme, or work with us to build a custom HubSpot theme
Build HubSpot Calculators & Interactive Conversion Tools
Make the most of Shopify themes. Connect with us to build a custom Shopify solution
Secure and scalable HubSpot web design for cybersecurity companies
In This Article
Updated: April 16, 2024
|
Published: April 15, 2019

Listen to the audio version
Web applications are a great way to get stuff done online, but they can be pretty vulnerable if proper action is not taken to secure them. For those that don’t know, webmail, online retail sales, and online auctions are all web applications, so you can notice the importance of using these safely and securely.
Here I’ll explain what you can do in order to protect your web applications with sensitive data from several different kinds of attacks. I’ve used Python 3 to write the web application script samples.
When using a web application, it needs to communicate with different kinds of incoming HTTP requests, which have two components. The components are a header and a payload. The payload is not involved in the shell shock attack; it is the header that is the weak link.
Any complex web application is configured to deal with a custom header, as each custom header can and usually conveys specific instructions for the web application.
In a shell shock attack, the hacker sends a malformed value for a custom header which results in execution of malicious code in the context of the web application.
The shell shock attack happens when a hacker sends a malformed value for a custom header, resulting in the execution of malicious code in the context of the web application. In more layman’s terms, the hacker will gain unauthorized access to the web application and the sensitive data it holds.
HTTP/1.x 200 OK .... Content-Type: text/html; charset=UTF-8 Last-Modified: Sat, 28 Nov 2009 03:50:37 GMT Custom-Malicious-Header: < Some Malicious Code >
The only defense one can implement against this kind of attack is to sanitize the custom header values. Also, the developer needs to ensure that their web application is not naïve to execute any code, and this way it has a fighting chance against the malicious code.
An XSS attack is the simplest and most used type of attack by hackers today. This attack starts by sending a malicious payload with the HTTP request to the web application. When the web application in question will execute the malicious payload, cross-site scripting happens, allowing the hackers to gain access to sensitive data contained within the web application.
Please follow the scenario below to see how a malicious script uses an XSS attack to gain access into a web application.
GET http:/target-host/?name=<script>alert(document.cookie);</script> HTTP/1.1
And lets say the web application renders the payload on the HTML page
import urllib.parse as urlparse
parsed = urlparse.urlparse(url)
name = urlparse.parse_qs(parsed.query)['name']
'''<html>
<head><title>My first Python CGI app</title></head>
<body>
<p> {} </p>
</body>
</html>'''
.format(name)
The main aspect of defending against an XSS attack is to sanitize the content. This includes avoiding sequencing and including the validation of the input against a pattern. See the figure below to determine how a proper web application code can be rewritten.
import urllib.parse as urlparse, cgi, re
parsed = urlparse.urlparse(url)
name = urlparse.parse_qs(parsed.query)['name']
# escape the special characters
escaped_name = cgi.escape(name)
''' match using regex if the name only contains alphabets,
numbers and spaces '''
pattern = re.compile("^([A-Z ][0-9]+)+$")
if pattern.match(escaped_name):
'''<html>
<head><title>My first Python CGI app</tit
le></h
ead>
<body>
<p> {}
</p>
</bo
dy>
</html>'''.format(escaped_name)
else:
print 'Name not valid'
If you look over the presented code, you will notice how some character were allowed and some are not. In our sample, I escaped the special character (<&>), and used a regular expression to ensure the name only has numbers, alphabets, and spaces.
A good way to defend against XSS is to define a content security policy that allows only a certain content will gain access to the web application. This can be seen in the web applications that use predefined content grammar language. One such application is Markdown.
A simple way to attack a web application is to stage a session (cookie) hijacking attack. In this attack, the hacker gains access to an already authenticated session key that the web application has issued to a client. This is done after successful completion of all the authorization and authentication processes, and anyone with this kind of access can make requests to the web application resources.
On the figure below you can see a session key hijacking by a man-in-middle attack and an XSS attack, but this can be done via a number of other means.
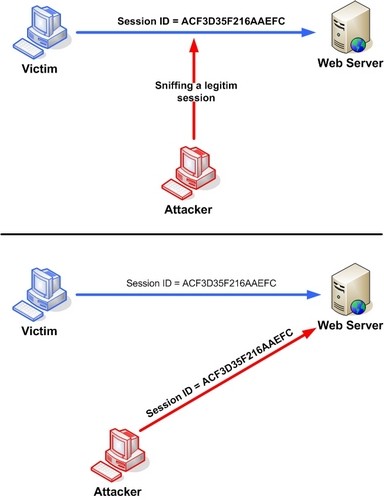
There are several ways to protect the web application against a session/cookie attack.
A JAR file can be embedded in a GIF or a PDD file, which can be executed by using an HTML <applet> tag. This is a basis for the attack, as JAR files are essential for the proper operating of a web application. In the case of infecting a JAR file to a GIF or PDF, the file becomes GIFAR/PDFAR and it provides access to the operating system resources which the hacker can’t get via a standard XSS attack. The access is usually executed via the code in the figure below.
<applet src="malicious-gifar.gif"></applet>
The best defense against this kind of attack is to validate the uploaded file. This is somewhat tricky to implement, but there are other things that can be done. A good way to protect is to disable the <applet> tag in the content security policy, as it will prevent the hackers to access the user data.
Also, it is smart to disable the Java plug-in in the browser, as it will prevent the embedding of a malicious JAR file.
Above I’ve discussed the most common attacks that happen on web applications today and explained the most common ways of protecting against them. Still, the Internet is a vast entity and is used by many, many creative people, some with not so honorable intentions.
My advice to all fellow web developers out there is to identify every possible vulnerability or threat you can think of and think of and implement a suitable fix. Anyone interested in further reading on securing websites and cyber security models can read more on LinkedIn.
.png?width=343&height=334&name=Frame%20(3).png)
.png?width=343&height=479&name=Frame%20(4).png)
Dive into our blog to discover a wealth of knowledge and expertise in the world of email services.
Protect your website and your reputation with pentesting Website penetration testing, better known as pentesting,...
Website and App Injection Vulnerabilities and How to Avoid Them Injection vulnerabilities are one of the most common...
As a business, your website is one of your biggest tools and can contribute to your growth, though the web design and...
A Quick Guide to HubSpot CMS Templates Who should read this articles: HubSpot-savvy marketers. Beginners who understand...
.png?width=204&height=62&name=Frame%20(13).png)
.png?width=204&height=62&name=Frame%20(18).png)
.png?width=204&height=62&name=Frame%20(11).png)
.png?width=204&height=62&name=Frame%20(12).png)
.png?width=204&height=62&name=Frame%20(15).png)
.png?width=204&height=62&name=Frame%20(16).png)
.png?width=204&height=62&name=Frame%20(17).png)
.png?width=204&height=62&name=Frame%20(17).png)
.png?width=194&height=62&name=Frame%20(20).png)
Copyright © 2025 HubBase, Inc.
